
An SQL injection vulnerability is a type of security exploit in which an attacker is able to input malicious code into a database by manipulating an SQL query. This can be done by using special characters or keywords in the input fields of a website that are not properly sanitized by the underlying code.
For example, let’s say a website has a login form that takes in a username and password. The website’s code then constructs an SQL query using the provided inputs, which looks something like this:
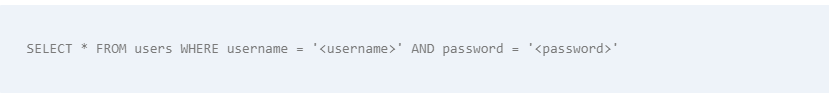
If an attacker were to enter the following into the username field:

The resulting SQL query would look like this:
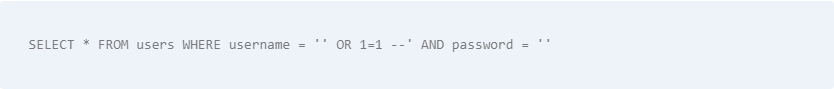
In this case, the attacker has successfully bypassed the login form and gained access to the website without providing a valid username or password. This is because the OR 1=1 condition always evaluates to true, and the -- is used to comment out the rest of the query, effectively ignoring the password check altogether.
In order to prevent this type of attack, it is important for web developers to properly sanitize user input and use prepared statements when constructing SQL queries. This can help to ensure that only valid data is input into the database, and that any malicious code is properly escaped or rejected.
Web Developer Tools can help with this by providing alerts and warnings when potentially dangerous input is detected, and by offering guidance on how to properly sanitize user input and avoid SQL injection vulnerabilities. Additionally, regular security audits and testing can help to identify and mitigate any security issues that may exist on a website.